How do crypto hardware wallets work? If you’re in the crypto space and haven’t asked yourself this question at least once and searched for the answer, you may be at more risk than you know. Most people hear about the importance of having a hardware wallet, and if they can afford to and are serious about crypto, they purchase one.
However, they are unaware of what risks the wallet is protecting them from and what risks they are still vulnerable to. In this article, you will learn the basics of a hardware wallet and what it can and can’t do to protect you.
Many people (including myself at one point) misunderstand the risks a hardware wallet mitigates. Not knowing what you are safe from is extremely dangerous and will give you a false sense of security toward your blockchain assets. I once foolishly thought it was impossible for a hacker to get at my NFTs as long as I stored them safely in my crypto wallet. As you read further, you will learn that that’s not true.
Why Learn How Crypto Hardware Wallets Work?
Before you learn how crypto hardware wallets work, you must understand a little about security online. To be able to manage the potential risks you may encounter, you need to first identify what risks there are. How can you implement steps to control risks without first understanding the risks you are trying to control or prevent?
Once you understand the risks, you should look for the best ways to control or prevent those risks and implement the controls. Once controls are implemented, test them.
Risks in the online space fall into one of three categories: Confidentiality, Integrity, and Availability. All risks will align with at least one of these principles, and they are foundational to security risk management
- Confidentiality – Ensuring that your data is kept private
- Integrity – Ensuring that your data is correct, authentic, and reliable
- Availability – Ensuring that your data is available when needed
How Do Crypto Hardware Wallets Work
Let me explain how these nifty little devices actually work. I remember being absolutely mystified when I got my first hardware wallet. How does this tiny thing protect millions in crypto? Let’s demystify it! First, think of a hardware wallet as a super-secure digital vault. You know those fancy bank vaults in movies with all the crazy security features?
A hardware wallet is kind of like that, but small enough to fit in your pocket. Pretty cool, right? Let me tell you about my first experience with one. I nervously set it up at my kitchen table, sweating bullets because I was about to transfer a decent chunk of crypto. I wondered, “How the heck will this little plastic thing keep my Bitcoin safe?” Well, turns out these devices are pretty ingenious.
Here’s the real magic: your crypto never actually “goes into” the wallet. Mind-blowing, right? Your coins always stay on the blockchain (I learned this the hard way after panicking when I thought my wallet had “lost” my crypto). What the hardware wallet stores are your private keys – basically, your super-secret password that proves you own your crypto. The genius part is how it handles these keys. Every hardware wallet has something called a “secure element chip” – think of it like a tiny fortress inside the device.
This chip is where all the important stuff happens. When you make a transaction, the signing happens inside this chip; your private keys never leave it. Not even you can extract them! I’ll never forget when I tried to explain this to my mom: “It’s like having a safety deposit box where the key is permanently locked inside, but you can still use it to sign checks.” She just stared at me blankly, but hey, I tried!
What Happens When You Use a Hardware Wallet:
- You plug it in or connect it via Bluetooth
- You enter your PIN (kinda like unlocking your phone, but way more secure)
- When you want to send crypto, the transaction details get sent to the wallet
- The wallet shows you the details on its screen (ALWAYS verify these!)
- If you approve, it signs the transaction inside that secure chip
- The signed transaction gets broadcast to the blockchain
But here’s where it gets really clever – the actual signing process happens in complete isolation. It’s like the wallet creates a little force field where no malware or hacker can peek at what’s happening. Pretty neat, huh? Now, let me tell you about when I learned the importance of that screen verification step. I almost sent many ETH to the wrong address because I didn’t double-check the details on the wallet’s display.
My heart still races thinking about that close call! Most hardware wallets also use something called “deterministic wallet generation.” Big fancy words, right? It means all your crypto addresses come from one master seed phrase (those 24 words you write down during setup). This is why backing up that seed phrase is CRUCIAL.
Speaking of seed phrases, here’s a pro tip I learned the embarrassing way: when you’re setting up your wallet and writing down those words, make sure you’re alone. I once had my webcam on during a video call while doing this. Rookie mistake! Thankfully, it was just a test wallet. The really cool thing about hardware wallets is how they handle different cryptocurrencies. Each coin type has its own “path” derived from your master seed. It’s like having a master key that can unlock multiple different vaults, each holding a different type of crypto.
One thing that still amazes me is how these devices can stay secure even if you plug them into a compromised computer. It’s like having an impenetrable bubble around your private keys. The wallet will show you exactly what you’re signing on its screen, so even if your computer’s been hacked, the hacker can’t trick you into sending funds elsewhere. But let’s be real – they’re not magic devices. They can’t protect you from yourself (trust me, I know).
No hardware wallet can save you if you share your seed phrase, approve a sketchy transaction, or fall for a phishing scam. It’s like having the world’s best lock on your door but then giving copies of the key to strangers. And remember, these devices aren’t indestructible. Keep them away from water, extreme temperatures, and curious pets. I learned that last when my cat knocked my first hardware wallet into a glass of water. Not my finest moment!
How To Protect Your Hardware Wallet
Here are some common risks encountered and how your hardware wallet protects you from them.
RISK #1 Seed phrase / private key theft is a confidentiality risk. The main goal of a hardware wallet is to provide a safe mechanism for interacting with the blockchain while mitigating the risk of an unauthorized entity gaining access to your seed phrase / private keys.
However, a hardware wallet does not keep your private keys safe on its own. If your backup (please ensure you always have a backup) is compromised, a scammer can use the private keys to access your assets regardless of your hardware wallet
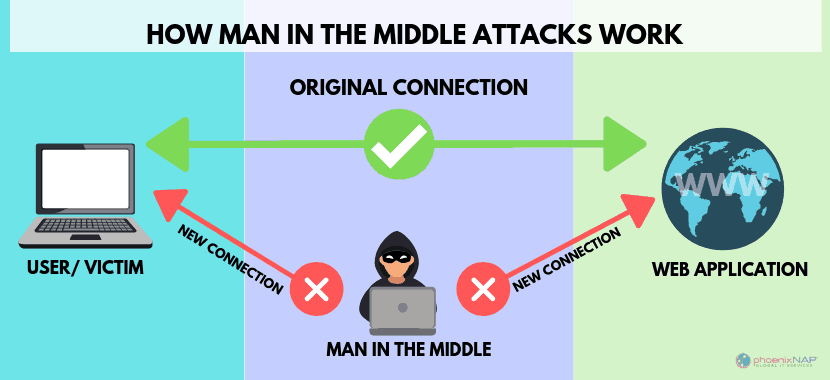
RISK #2 Man-in-the-middle signature – This is an integrity risk. Although your hardware wallet wasn’t specifically created to fight against this type of risk, it also protects you against it. There is a risk that your metamask on your PC/phone could be compromised, and you sign an unexpected transaction that looks legitimate (which happened to me once).
Everything will look like the original transaction you tried to approve while taking your signature and applying it to a separate illegitimate transaction. You will not know this is happening if you only use a software/hot wallet.
If you are using a hardware wallet, it will always show the actual transaction on your screen as you sign it. If you find that the way transactions pop up to be approved is often difficult to read, try gridplus Lattice1, as it has the capability to show you what you are signing in human-readable form (not hex).
What risks are you still vulnerable to?
You may still be affected by many risks if you’re not careful. This article does not go in-depth into all the risks, but here are a few listed below:
- NFT / ETH drains—These often happen on fake mint sites and are more common than you might think. They essentially happen because you approve these with your hardware wallet.
- Seed phrase backup theft happens when your PC or mobile is hacked or compromised, and your seed phrase is taken. Never store your seed phrase on your devices or anywhere online.
- Seed phrase loss due to lack of backup happens when you misplace or lose your seed phrase and cannot provide it when requested.
- Losing staked NFTs due to contract hack occurs when the contract holding the nft you have staked is hacked.
Security Tests
Now that you understand the risks/controls you need to be aware of and have bought and set up an appropriate hardware wallet, you have to test the controls you implemented to ensure they do what they’re supposed to do. To do this, simply attempt a transaction from your software wallet without your hardware wallet connected.
Does the transaction succeed? If it does, your software wallet holds your keys, and you are still at risk. You must transfer your assets to an address derived from the seed phrase only in your hardware wallet. YOU SHOULD NEVER IMPORT THIS PHRASE INTO A SOFTWARE WALLET!
Many people find that their wallet behaves oddly, only to find that they had imported the seed phrase from their hardware wallet into Metamask. If you have done this, you are NOT SAFE. Create a new seed phrase on your hardware wallet and transfer your assets ASAP.
Final Thoughts
The bottom line? Hardware wallets are like having your own personal bank vault, complete with military-grade security, all in a package small enough to carry in your pocket. Just remember – the security is only as good as the person using it. Now that you understand how hardware wallets work and what they protect you from check out this article on keeping your crypto safe and saving money.If you’ve enjoyed this article, please comment below if you think anything else was left out. Also, do you have any particular subjects that you would like me to cover in future articles?
Frequently Asked Questions
How do crypto hardware wallets work to keep my investments safe?
Crypto hardware wallets work by storing your private keys offline, away from potential online threats. This means that even if your computer is compromised, your cryptocurrencies remain secure on the hardware device.
How do crypto hardware wallets work when I want to make transactions?
When you want to make a transaction, a crypto hardware wallet signs the transaction within the device itself. It generates the necessary signatures without exposing your private keys to the internet, ensuring your funds remain protected.
How do crypto hardware wallets work compared to software wallets?
Crypto hardware wallets provide enhanced security compared to software wallets by keeping your private keys offline. While software wallets are more convenient for quick access, hardware wallets are ideal for long-term storage and protecting larger amounts of cryptocurrency.
How do crypto hardware wallets work for beginners who are new to investing in cryptocurrency?
For beginners, crypto hardware wallets work by offering a simple and secure way to manage digital assets. They often come with user-friendly interfaces and guides, making it easy to set up, navigate, and understand how to safely store and use your cryptocurrencies.








![[secure bitcoin wallets]](https://cryptohashira.com/wp-content/uploads/2024/11/1730320405725x325769434323760060-feature-120x86.png)

![[crypto asset security]](https://cryptohashira.com/wp-content/uploads/2024/11/1730320405711x482955841305053900-feature-120x86.webp)
