Since diving into the thrilling crypto world in 2019, I’ve navigated many of its challenges, including some tough security lessons. It’s astonishing to think that in 2022 alone, more than $3.8 billion in crypto assets were lost due to hacks and scams! I vividly recall a night when I nearly fell victim to a phishing scam—what an eye-opener that was!
This journey has truly reinforced for me the vital importance of learning to secure your crypto assets and staying alert to potential threats. When you’re first getting into crypto, security can seem overwhelming. All these fancy terms are being thrown around—private keys, seed phrases, hardware wallets—and it’s honestly pretty confusing! But after teaching hundreds of students about crypto security (and learning some painful lessons myself), I’ve figured out how to make this stuff actually make sense.
In this guide, I’ll walk you through everything I wish someone had told me when I first started. There will be no fancy jargon or complicated technical stuff—just practical, tested advice from someone who’s been in the trenches. Trust me, by the end of this, you’ll know exactly how to keep your crypto safe!
Why You Secure Your Crypto Assets
You know what’s wild? When I first got into crypto, I thought keeping my Bitcoin on an exchange was totally fine. I mean, that’s what we do with regular banks, right? Boy, was I wrong! Here’s the thing about crypto that differentiates it from your regular bank account: when you own crypto, you’re basically your own bank. That’s both awesome and terrifying! Instead of having a password you can reset or a bank you can call, you have private keys.
Think of them like the master key to your digital vault—if you lose them, you’re toast. If someone else gets them, you’re also toast. Fun right? I remember this one time when I stored my private key in my email drafts (I know, I know—rookie mistake!). I thought I was being clever, but then I learned how easily email accounts can be hacked.
Nowadays, I literally cringe thinking about it. Let’s simplify things. Your public address is like your email address—you can share it with anyone who wants to send you crypto. But your private key? That’s like the password to your email account, except it’s about a million times more important because you can’t ever reset it. The most common security problems I see with newbies usually stem from their lack of understanding of these basics.
They’ll do things like taking screenshots of their private keys (please don’t!) or sharing them with someone who’s “trying to help” (definitely don’t!). Here’s a lesson I learned the hard way: In crypto, security isn’t just about keeping bad guys out—it’s about protecting yourself from, well, yourself! I can’t tell you how often I’ve almost messed up by trying to access my wallet when I was half asleep or rushing to make a trade.
Essential Hardware Wallet Security
Okay, real talk—getting my first hardware wallet was a game-changer. But whew, setting it up was an adventure! I remember sitting at my desk, sweating bullets as I transferred my first big chunk of Bitcoin to it. The whole time, I kept thinking, “Please don’t let me mess this up!” Hardware wallets are like tiny, super-secure computers that completely keep your crypto keys offline.
Think of them as your crypto fortress—even if your regular computer gets hacked, your crypto stays safe. Unless you’re like my friend Mike, who wrote his seed phrase on a sticky note and stuck it to his monitor (spoiler alert: don’t be like Mike!). I personally use a Ledger Nano X (though there are other great options like Trezor).
Whatever you choose, you can check out the setup process that’s helping dozens of people get started. First things first: only buy your hardware wallet directly from the manufacturer. I learned this the hard way when I almost bought one from a random Amazon seller (thankfully, someone warned me in time!). These things need to be factory-fresh and untampered with.
When you’re setting up your wallet, find a private place—no webcams, no people peeking over your shoulder, and definitely no “helpful” YouTube tutorials running in the background. Trust me, I’ve heard some horror stories about people following compromised setup videos.
The most nerve-wracking part? Writing down your backup phrase. These 24 words are literally the keys to your crypto kingdom. I keep mine etched on a steel plate (fire-proof, water-proof, pretty much everything-proof), split between two different locations. Sounds paranoid? Maybe, but after seeing what happened to a student who lost their crypto in a house fire, I’d rather be safe than sorry!
If you want more info on the differences between wallets, check out this post on hardware vs. software wallets.

Software Wallet Best Practices
Can I be real with you for a minute? Software wallets are like that friend who’s super convenient to have around but sometimes gets you into trouble! I use them all the time for smaller amounts, but man, I’ve had some close calls. I once showed off my new crypto wallet app to a friend at a coffee shop. I didn’t think twice about being on public WiFi—a rookie mistake!
Thankfully, I only had a small amount in there, but it was enough to teach me a valuable lesson about when and where to access my crypto. Here’s my rule of thumb: software wallets are great for what I call “crypto pocket money”—small amounts you might need quick access to.
I personally use MetaMask for my day-to-day stuff, but I never keep more in there than I’d be willing to lose. It’s kind of like carrying cash—you wouldn’t walk around with your life savings in your pocket, right?
Here’s what to look for in a good software wallet:
- Built-in browser security (MetaMask is pretty good at warning you about sketchy websites)
- Solid backup options (please, please back up your seed phrase!)
- Regular security updates (if your wallet app hasn’t been updated in months, run!)
The biggest mistake I see people make with software wallets is treating them like they’re as secure as a cold storage wallet. They’re not! I had friends who kept their entire crypto portfolio in a hot wallet because it was “more convenient.” Guess what happened? Yeah, it wasn’t pretty.
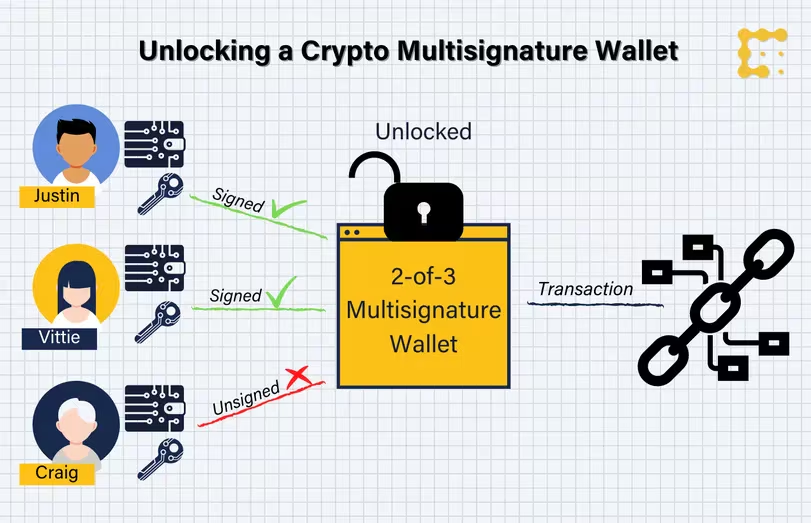
Creating an Unbreakable Security System
Listen, I will let you in on a little secret—there’s no such thing as a completely unbreakable crypto asset protection system. But boy, can we make it really, really hard for the bad guys! After years of trial and error (mostly error, if I’m honest), I’ve developed what I call my “paranoid but practical” approach. Setting up a multi-signature wallet was a game changer for me.
Imagine needing three different keys to open your safe instead of just one. Sounds like a pain, right? Well, it kind of is, but it’s saved my back more than once! I remember this one time when my computer got compromised, but because I needed additional signatures from different devices, my crypto stayed safe and sound.
Here’s my current setup (which I wish I’d had years ago):
- Cold storage for the bulk of my holdings (hardware wallet kept in a secure location)
- Hot wallet for active trading (but never more than 5% of my total holdings)
- Multi-sig setup for large amounts (requires approval from multiple devices)
Testing your security setup is crucial, and boy, did I learn this the hard way! I once thought I had the perfect backup system until I actually needed to use it. It turns out I’d written down one of my recovery phrases incorrectly. Now, I do a complete test restore every few months—it’s a pain but way less painful than losing everything!

Protecting Against Social Engineering
Can we talk about social engineering for a minute? This stuff keeps me up at night! You wouldn’t believe some of the clever scams I’ve seen—actually, you probably would because these scammers are everywhere in crypto! I’ll never forget when I almost fell for a fake “urgent security update” from what looked exactly like my wallet provider.
The email and website looked perfect, but the only thing that saved me was my personal rule: never click on links in crypto-related emails. Here’s the thing about crypto scammers: they’re not trying to hack your technology but your brain!
They know exactly which emotional buttons to push. FOMO? They’ve got a fake “exclusive” presale for you. Fear? They’ll send you urgent warnings about your wallet being “compromised.” Greed? Let’s just say if someone promises to double your crypto, they plan to double their own! I’ve developed what I call my “paranoid pause” technique.
Before doing anything with my crypto, I stop and ask:
- Did I initiate this interaction?
- Is someone rushing me to make a decision?
- Does this sound too good to be true?
- Am I being asked to share sensitive information?
And don’t even get me started on passwords! I used to use the same password everywhere (I know, I know) until a platform I used got hacked. Now, I use a password manager and generate unique passwords for everything. Yes, it’s annoying sometimes, but not as annoying as getting hacked!

Recovery and Inheritance Planning
This is the part nobody likes to talk about, but we need to. What happens to your crypto if something happens to you? I put this off for years until a close friend passed away suddenly, and his family had no idea how to access his crypto. That was the wake-up call I needed. Creating a crypto will isn’t fun—I procrastinated on this for months!
But it was such a relief once I finally sat down and did it. I’ve set up what I call my “crypto legacy plan,” and while it’s not perfect, it’s better than nothing. The trickiest part was figuring out how to make my crypto accessible to my family without making it vulnerable.
You can’t exactly write your seed phrase in a regular will (that becomes a public document!). I used a combination of safe deposit boxes, trusted attorneys, and what we call a “dead man’s switch”—basically, if I don’t check in regularly, instructions get sent to specific people.
Here’s what I’ve learned about inheritance planning:
- Keep instructions crystal clear (your family might not know anything about crypto)
- Don’t put all the access information in one place
- Make sure at least two trusted people know about your plan
- Update your instructions whenever you make significant changes
Final Thoughts
Whew! We’ve covered a lot of ground here, haven’t we? I know all this security stuff can feel overwhelming—I’ve been there! But here’s the thing: you don’t have to implement everything at once. Start with the basics: get a hardware wallet, secure your seed phrases, and be super careful about who you trust with your crypto information.
If you follow the correct steps to store cryptocurrency, you should be okay. Remember that time I mentioned almost losing my Bitcoin to a phishing attack? Well, that scared me straight into taking security seriously, but you don’t have to learn things the hard way like I did. Take it one step at a time, and keep building your security practices as you go.
Why not start today? Pick just one thing from this guide—maybe backing up your seed phrase properly or setting up a hardware wallet—and get it done. Your future self will thank you!
Do you have your own crypto security stories or tips to share? Drop them in the comments below! And remember—in crypto, you are your own bank. Take that responsibility seriously, but don’t let it paralyze you. Stay safe out there, cryptofam!
Frequently Asked Questions
How can I effectively secure my crypto assets?
To effectively secure your crypto assets, use hardware wallets for offline storage, enable two-factor authentication on your exchanges, and regularly update your passwords to keep your accounts safe.
What are the best practices to secure my crypto assets?
Best practices to secure your crypto assets include using strong, unique passwords, keeping your recovery phrases private, and being cautious of phishing attempts by verifying links before clicking.
Should I use a software wallet or a hardware wallet to secure my crypto assets?
A hardware wallet is generally considered safer for securing your crypto assets because it stores your private keys offline, reducing the risk of hacks compared to software wallets.
How often should I review my strategies to secure my crypto assets?
It’s a good idea to review your strategies to secure your crypto assets at least every few months or whenever there are major developments in the crypto space, ensuring your security measures remain up-to-date.
What should I do if I suspect my crypto assets are compromised?
If you suspect your crypto assets are compromised, immediately transfer your funds to a secure wallet, change your passwords, enable two-factor authentication, and check for any unauthorized transactions.

![[secure bitcoin wallets]](https://cryptohashira.com/wp-content/uploads/2024/11/1730320405725x325769434323760060-feature-120x86.png)


![[secure bitcoin wallets]](https://cryptohashira.com/wp-content/uploads/2024/11/1730320405725x325769434323760060-feature-350x250.png)

![[crypto asset security]](https://cryptohashira.com/wp-content/uploads/2024/11/1730320405711x482955841305053900-feature-350x250.png)








![[crypto asset security]](https://cryptohashira.com/wp-content/uploads/2024/11/1730320405711x482955841305053900-feature-120x86.webp)
